Kubernetes is a powerful tool for managing applications, but it requires proper security measures. Think of your Kubernetes cluster as a fortress. This guide will help you reinforce its walls and protect your valuable data inside.
Why Security Matters
Leaving your Kubernetes cluster unsecured is akin to leaving the gates of your fortress wide open. Attackers could sneak in, steal your data, or even take control of your applications. Security hardening is like bolstering your defenses, making it much harder for attackers to breach your fortress.
Key Areas to Secure
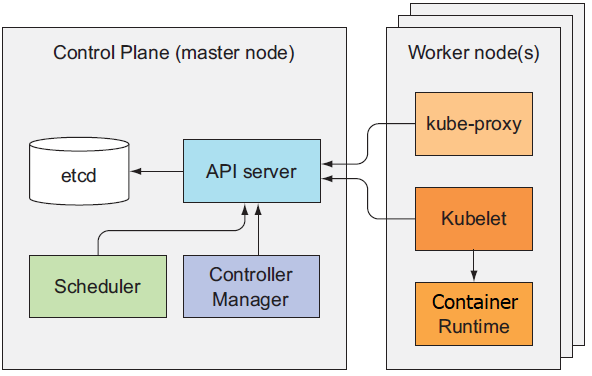
1. The Command Center (Control Plane)
This is the brain of your fortress. Protecting it is crucial.
-
Limited Access (RBAC): Not everyone needs access to everything. RBAC (Role-Based Access Control) is like giving specific keys to different people. Only grant the minimum necessary access. Avoid giving anyone the “master key” (
cluster-admin) unless absolutely essential. - Protected Secrets (etcd): etcd is the vault where your fortress’s most sensitive information is kept. Encrypt it both at rest and in transit. Learn more about etcd security.
- Activity Logs (Audit Logging): Keep a detailed record of everything that happens in your fortress. This helps you spot suspicious activity and troubleshoot issues. Check out logging best practices.
2. The Walls (Worker Nodes)
These are the foundations of your fortress, where your applications run.
- Regular Maintenance (Updates): Just like real walls need repairs, your worker nodes need regular updates to patch security holes. Read about update strategies.
- Internal Firewalls (Network Policies): Control the flow of traffic within your fortress. Prevent unauthorized communication between different parts of your applications. Explore network policies.
- Reinforced Doors (Security Contexts): Add extra layers of security to individual applications (pods) by restricting their access to resources. See more on security contexts.
3. The Supplies (Container Images)
These are the resources your applications need to function.
- Trusted Suppliers (Trusted Images): Only accept supplies from trusted sources. For a reliable Kubernetes environment, consider using Trusted Image Resource.
- Supply Inspection (Image Scanning): Inspect your supplies for hidden dangers. Scan container images for vulnerabilities using Image Scanning Tools.
- Secure Storage (Pod Security Admission): Define rules to ensure that only secure supplies are allowed into your fortress. Learn about pod security.
4. The Treasure (Secrets Management)
Protect your most valuable assets.
- Hidden Vaults (Kubernetes Secrets): Store sensitive information like passwords and API keys securely using Kubernetes Secrets. Encrypt them at rest. Find out more about secrets management.
- Fort Knox (Dedicated Secret Management): For even greater security, consider using Dedicated Secret Management Solutions.
5. The Perimeter (Network Security)
Control access to your fortress.
- Guarded Gates (Ingress Control): Manage who can enter and leave your fortress. Use Ingress controllers and configure them securely. Learn about ingress control.
- Outer Walls (Firewall Rules): Build a strong perimeter around your fortress to block unwanted traffic. Read about firewall best practices.
Getting Started – First Steps
- Security Checkup (Security Audit Tool): Use a security audit tool to identify weaknesses in your fortress. Check out top security audit tools.
- Read the Manual (Kubernetes Documentation): Consult the official Kubernetes documentation for security best practices. Visit Kubernetes Documentation.
- Start Small: For those new to Kubernetes, check out courses on Learning Platforms for comprehensive learning.
Conclusion
Securing your Kubernetes fortress is an ongoing effort. By following these steps and staying informed about the latest security practices, you can significantly strengthen your defenses and protect your valuable applications and data.