What is Amazon EKS
Amazon Elastic Kubernetes Service (Amazon EKS) is a managed Kubernetes service that eliminates the need to operate and maintain the availability and scalability of Kubernetes clusters in Amazon Web Services (AWS) and in your own data centre’s.
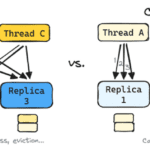
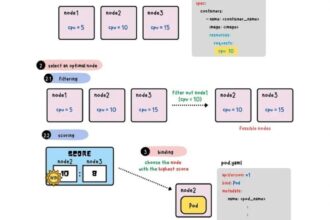
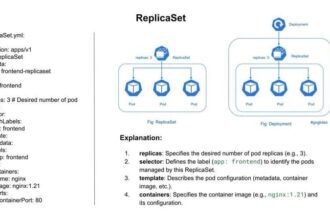
Kubernetes: is an open source system that automates the management, scaling, and deployment of containerised applications.
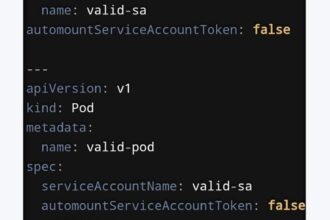
Amazon Elastic Kubernetes Service (EKS) is rolling out a major security enhancement for Kubernetes users: default envelope encryption **for all Kubernetes API data in clusters running **version 1.28 or higher. This update integrates AWS Key Management Service (KMS) with Kubernetes KMS provider v2, delivering a fully managed, defense-in-depth security layer for your Kubernetes applications — straight out of the box.
What’s Changing?
Previously, envelope encryption in EKS was an optional feature, available through KMS provider v1. With this update, it becomes the default configuration for all Kubernetes API objects. AWS will now provide a default KMS encryption key, but you still have the flexibility to create or import your own keys into AWS KMS for your cluster’s control plane.
If you’ve already been using a customer-managed key (CMK) to encrypt Kubernetes Secrets, the same key will seamlessly extend to encrypt additional API data types in your cluster — no additional configuration needed.
Why This Matters for DevOps Engineers
This update simplifies security management for Kubernetes workloads:
Reduced Configuration Overhead: No need to manually enable encryption; it’s built-in by default.
Seamless CMK Integration: If you’re already using a CMK, no extra steps are required to extend encryption across API data.
Stronger Security & Compliance: Automatically enhances data protection without increasing operational complexity.
More Time for Innovation: Focus on delivering applications, not configuring encryption settings.
For teams prioritising security and compliance, this change reinforces data protection while maintaining flexibility. Whether you’re a seasoned cloud architect or a DevOps engineer managing multiple clusters, this update means one less security concern to worry about.
What do you think, how will this impact your workflows? Let’s discuss below!